Source: iStock.com/BrianAJackson
Source: iStock.com/BrianAJackson
Working from home Office attracts vishers
7. October 2020 Published by Raphael DoerrTo set things straight right away: Vishers are not fishers, a vishing call is not a call from a fisher, and vishing definitely has nothing to do with fishing.
According to the definition of the German Federal Office for Information Security (BSI), the term “vishing” stands for “voice phishing” or “phishing via VoIP” and refers to organized data theft by phone. And, as with phishing, the aim of the attackers is to gain access to sensitive information of the potential victims. Unlike phishing, however, the preferred medium is not the Internet or e-mail. A vishing attack can be carried out by phone call on the landline, mobile phone or as a voice message. The attackers also often use VoIP technology.
It may appear a little old-fashioned, but criminals still like using the phone. In fact, they rely on many people regarding the phone as a trustworthy form of communication.

The FBI is currently warning about vishing campaigns
Due to the pandemic, more and more people are working from home and, as a result, are often unknowingly ideal victims for vishing scams due to the lack of security solutions. In the U.S., the FBI and the American Cybersecurity Infrastructure Security Agency (“CISA”) issued a leaflet in August of this year to inform companies of a vishing campaign by cybercriminals:
“The COVID-19 pandemic has resulted in a mass shift to working from home, resulting in increased use of corporate virtual private networks (VPNs) and elimination of in-person verification. In mid-July 2020, cybercriminals started a vishing campaign -gaining access to employee tools at multiple companies with indiscriminate targeting—with the end goal of monetizing the access. Using vished credentials, cybercriminals mined the victim company databases for their customers’ personal information to leverage in other attacks. The monetizing method varied depending on the company but was highly aggressive with a tight timeline between the initial breach and the disruptive cashout scheme.”
As a fraud tactic, vishing is no newcomer and has been known for years. Back in 2012, the security expert McAfee already warned about it on its website: „Vishing” occurs when criminals cold-call victims and attempt to persuade them to divulge personal information over the phone. These scammers are generally after credit card numbers and personal identifying information, which can then be used to commit financial theft. Vishing can occur both on your landline phone or via your mobile phone.”
But unlike before, where the attacks were mostly aimed at elderly or vulnerable people, more and more companies and their employees are now becoming the target of the attackers. Cybercriminals are using the weaknesses in the security protocols in remote working from home. Their aim is to gain access to a company’s confidential or protected business information via the virtual private network (“VPN”) with the help of its own employees in order to then blackmail the company. VPNs are often used in the current teleworking environment and are supposed to be a secure platform for remote employees to log into their company’s network from home.
The online magazine daily-it.net describes on its website what such an attack might look like
Data security and trust infrastructure with remote IT
“An employee at the targeted company working from home receives a series of phone calls. The criminals claim to be calling from the company’s IT department and needing to eliminate problems with the VPN connection. Their aim is to get the employees to divulge their access data either over the phone or on a fake Internet site that could easily be mistaken for the targeted company’s e-mail or VPN portal. This site’s address resembles the name of the company and additionally includes abbreviations such as “vpn”, “ticket” or “portal”.
Functioning links to genuine online resources can even be integrated on the phishing site. The attackers concentrate primarily on new employees and claim to be new to the IT department themselves. To appear more credible, they even set up profiles on LinkedIn and attempt to use them to network with other employees at the targeted company. That creates the impression that the fake profile actually belongs to a real employee at the company. Speed is of the essence for the perpetrators in this type of attack, since many companies rely on multi-factor authentication for VPN access. That means, in addition to the user name and password, that additional information is required to log in. And this information – for example, a unique code generated by an app or sent to the employee by SMS – is often only valid for a short period. The criminals bypass these security measures by simply also asking for this additional factor on their phishing sites. If the victims divulge their login information right over the phone, the criminals can log into the VPN in real time before the additional code is no longer valid.
Voice phishing – figures
According to the German computer magazine Computerwoche, phishing by voice call has already become well established:
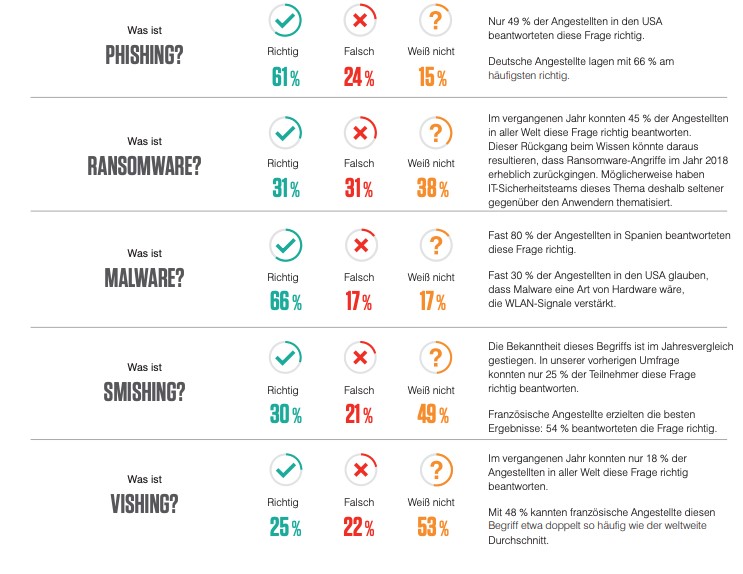
- Vishing attacks have been multiplying for years – in 2018, around 30 percent of all incoming calls were of a fraudulent nature.
- According to Proofpoint’s report “State of the Phish 2020”, only 25 percent of the surveyed employees can define the term correctly.
- 75 percent of the vishing victims said that the attackers were in possession of personal information about them that was used to continue the attack.
Call until someone picks up
The convenient option of sending digital voice signals over the Internet has led in the last few years to a huge increase in spam calls and robocalls. According to Hiya, a company that offers anti-spam telephone solutions, the number of spam calls in 2019 even rose to 54.6 billion, making it an increase of 108% over the previous year. Since a computer-based autodialer is used for robocalls to play previously recorded messages, marketing experts and fraudsters can make far more calls than would be possible for a living person. They often use tricks and, by using a fake area code, for example, make it appear as if the call is from the recipient’s region. That increases the probability of the call being taken, since the caller thinks it’s from a family member, friend or their company.
How to protect yourself
Users such as consumers can protect themselves by remaining vigilant with every unexpected message, irrespective of the medium or source from which it reaches them. The U.S. agency FTC provides several tips on its website on how people can identify and prevent vishing attacks:
- Be suspicious of calls from government agencies asking you for money or personal information. That’s not how any government agency operates. If in doubt, end the conversation and call the official number of the agency to make sure.
- Never pay by phone in the form of a credit, gift card or bank transfer.
 Comments
Comments
 en
en